Jamie Smith’s Portfolio
Professional Highlights
Here’s an example of some of the public-facing professional collateral that I’ve put together over the past few years. It’s not an exhaustive list, and as time passes some things might have been replaced or removed.
|
Elastic Observability Video 2021 I wrote the script, storyboarded the animations, and narrated this video which was on the solution landing page for over a year |
|
Monitoring Applications with Elasticsearch and Elastic APM January 30, 2019 This was the overall top observability blog for both overall hits and time on page) was leveraged across the funnel- for onboarding, nurture flows, CTAs, etc. This blog helped kicked off an extremely successful APM awareness campaign. |
|
|
SnykLaunch April 2023 - Curated container security workflows April 4, 2023 This was a launch webinar for Snyk’s Custom Base Image Recommendations, where I served as the SME with the product manager, to help spread awareness of a new feature that extended what was, at the time, Snyk Container’s key differentiator. I also wrote a post-launch blog, SnykLaunch recap: Custom Base Image Recommendations |
|
Securing Your Modern Software Supply Chain 2022? This software supply chain security article was used as a landing page in a successful GTM/ TOFU/MOFU campaign |
|

|
Introduction to logging with the ELK/Elastic Stack 2020 This presentation/webinar was a fun one, focused on how to get started using the Elastic Stack for log and metrics analytics — the first steps on the path to observability. |
|
Going beyond reachability to prioritize what matters most October 1, 2024 This was one of the cornerstone pieces for the “Holistic risk-based prioritization” campaign that we used in 25q1. Reachability is one signal, but not the only signal (and probably not the most important) |

|

|
Leveraging observability to build better applications (eBook) (Ungated version) |
|
Lessons from OpenSSL vulnerabilities part 1: Preparing your supply chain for the next critical vulnerability April 19, 2023 This is a two-part series on some OpenSSL vulns that were discovered in older versions. This is part one, where we go over some abstract, high-level concepts to think about when the next zero-day drops |

|

|
Lessons from OpenSSL vulnerabilities part 2: Finding and fixing supply chain vulnerabilities April 26, 2023 This second part moves past the theory and walks through some of the ways to be ready for the next zero-day |
|
But First, Coffee... (An Elastic{ON} Canvas Story) March 14, 2018 This one’s in here because it’s actually one of my favorite blogs. It was a fun project and fun blog. It is also what got me hooked on home automation. Plus, I really like coffee |
|
Other interesting webinars
|
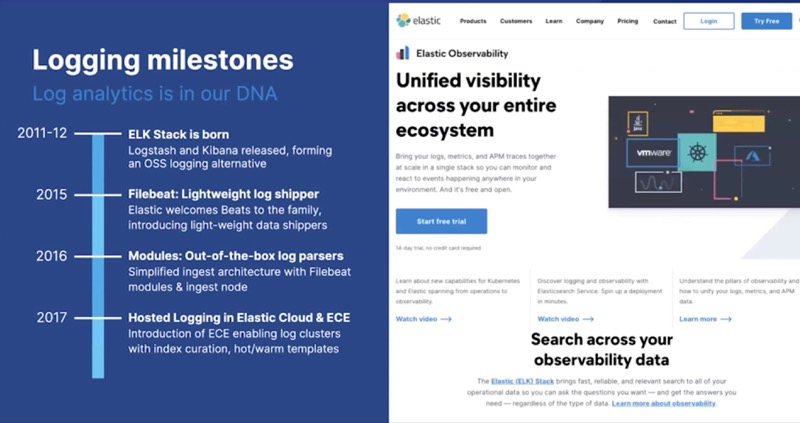
Evolution of logging with the Elastic Stack The Elastic Stack (or ELK Stack) had long been an enterprise standard for centralized logging, but they continued evolving the platform. |
|
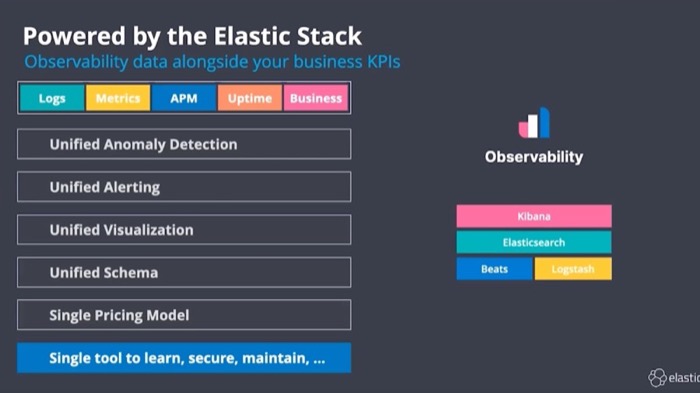
Combining logs, metrics, and traces for unified observability This was part of a launch event. When Elastic started marketing an “observability solution”, the term “Observability” wasn’t yet widely used (in fact, Gartner still just calls all of it “APM”). This was one of the first events that we actually leaned in on the term |
|

|
SnykLaunch April 2023 - Curated container security workflows April 4, 2023 This was a launch webinar for Snyk’s Custom Base Image Recommendations, where I served as the SME with the product manager, to help spread awareness of a new feature that extended what was, at the time, Snyk Container’s key differentiator. I also wrote a post-launch blog, SnykLaunch recap: Custom Base Image Recommendations |
Product/Solution Pages
(Note that it’s likely that these will get changed in the future, but accurate as of August 5, 2025)
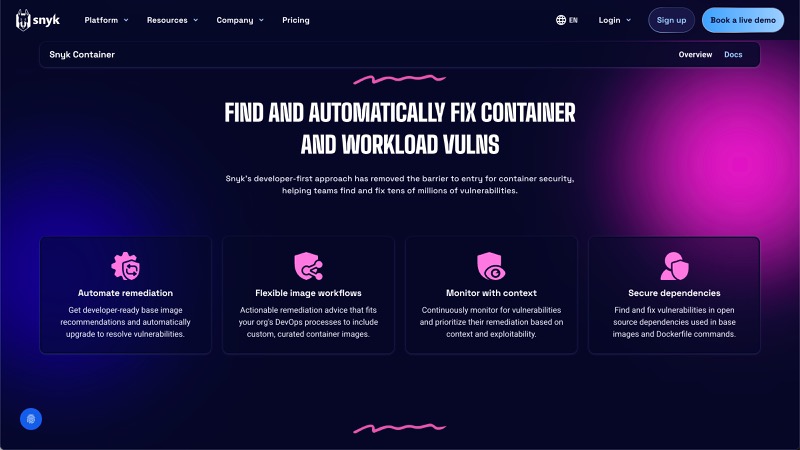
|
The Snyk Container Security landing page This also had a one-pager layout for events |
|
The Software Supply Chain Security Solution landing page we also created a one-pager variant of this page which was used as a virtual handout for webinars |

|
Other Blogs from Snyk

|
Snyk-Generated SBOMs Now Include License Details for the Open Source Libraries in Your Projects December 9, 2024 Snyk now includes license information in its generated SBOMs, giving developers a clearer picture of their application’s components and associated license risks and simplifying compliance and security… |
|
2024 Open Source Security Report: Slowing Progress and New Challenges for DevSecOps December 3, 2024 Read top-level findings from Snyk’s 2024 Open Source Security Report, exploring slowing progress and new challenges for DevSecOps. |
|

|
Going beyond reachability to prioritize what matters most October 1, 2024 While static reachability can help teams better understand their app vulnerabilities, they must be paired with other types of context and risk insights. |
|
Weak Hash vulnerability discovered in crypto-js and crypto-es (CVE-2023-46233 & CVE-2023-46133) October 25, 2023 (This was a zero-day reporting) |

|
|
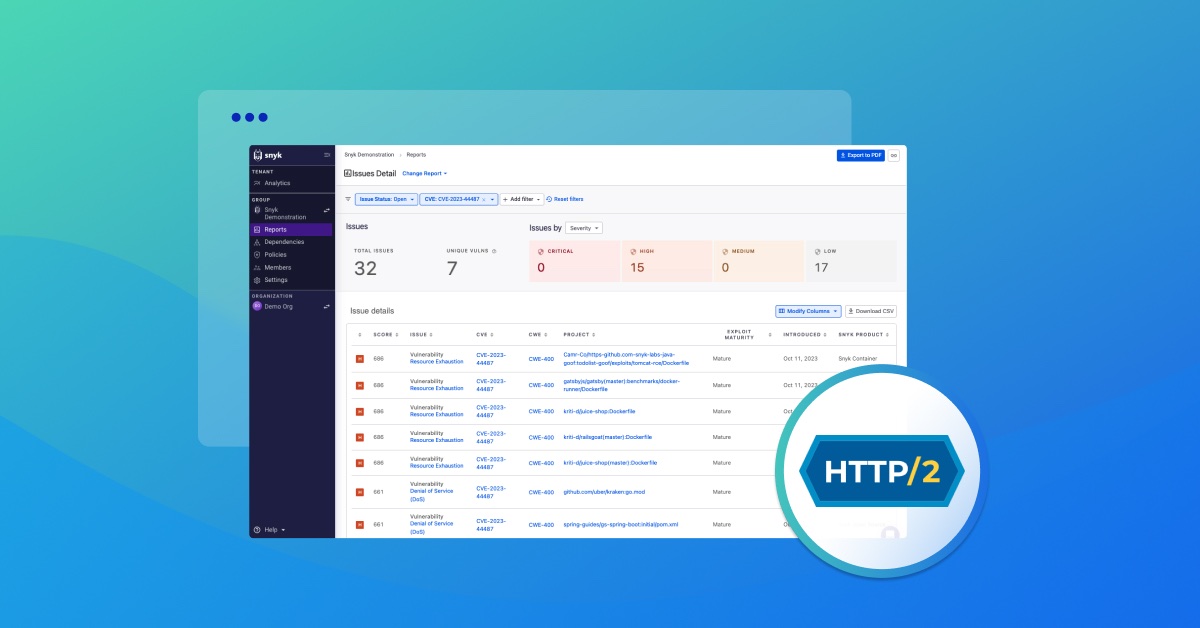
Find and fix HTTP/2 rapid reset zero-day vulnerability CVE-2023-44487 October 11, 2023 (This was a zero-day reporting) |
|
Developer-first supply chain security September 19, 2023 Developer-first supply chain security aims to minimize the risk of potential breaches, streamline the development workflow, foster collaboration, and instill a culture of vigilance. |

|

|
Software Supply Chain Security Tools: Types, Features & Considerations August 2, 2023 Software supply chain security tools provide a range of features to identify and mitigate potential risks and vulnerabilities in your supply chain. |
|
Secrets Management: Tools & Best Practice June 26, 2023 As applications and projects scale, so will the number of secrets you need to keep safe. Learn the best practices and tools to use to secure your secrets. |

|

|
High profile AWS breaches & how to avoid them June 7, 2023 This was mostly a consolidation piece, summarizing some recent breaches for companies like Capital One, Twilio, and Uber have all suffered from AWS breaches. Learn from their experiences and prevent the next breach from happening to you. |
|
Lessons from OpenSSL vulnerabilities part 1: Preparing your supply chain for the next critical vulnerability April 19, 2023 In this two part series, we’ll walk through some of the things you need to consider when finding instances of a vulnerability in your software supply chain. Let’s begin by discussing where you’ll need… |

|

|
Lessons from OpenSSL vulnerabilities part 2: Finding and fixing supply chain vulnerabilities April 26, 2023 This software supply chain security series centers on the lessons learned from OpenSSL and what you need to consider when enhancing your supply chain security. |
|
SnykLaunch recap: Custom Base Image Recommendations April 4, 2023 One of the exciting new features discussed at SnykLaunch today was Custom Base Image Recommendations (CBIR). Read on for all the details. |

|

|
Top AWS Security Risks & Prevention March 1, 2023 Check out the top 10 challenges and risks to your AWS security. Follow our best practices to secure your AWS deployments and avoid security mistakes or misconfigurations. |
|
Three ways Snyk made software supply chains more secure in 2022 January 12, 2023 In 2022, Snyk continued to expand on our developer-centric approach to software security, by adding several key enhancements to the existing solutions — let’s focus on three key capabilities introduce… |

|
Other Blogs from Elastic

|
What's new in Elastic Observability 7.13: Native Azure console integration, Fleet Server, and enhanced APM workflows 25 May 2021 Elastic Observability 7.13 adds native integration in Azure console, the new Fleet Server, new troubleshooting views in Elastic APM, and more… |
|
Getting started with free and open Elastic Observability 21 April 2021 Learn how to get started with free and open Elastic Observability, including downloading, installing, enabling security, and loading sample data… |

|
|
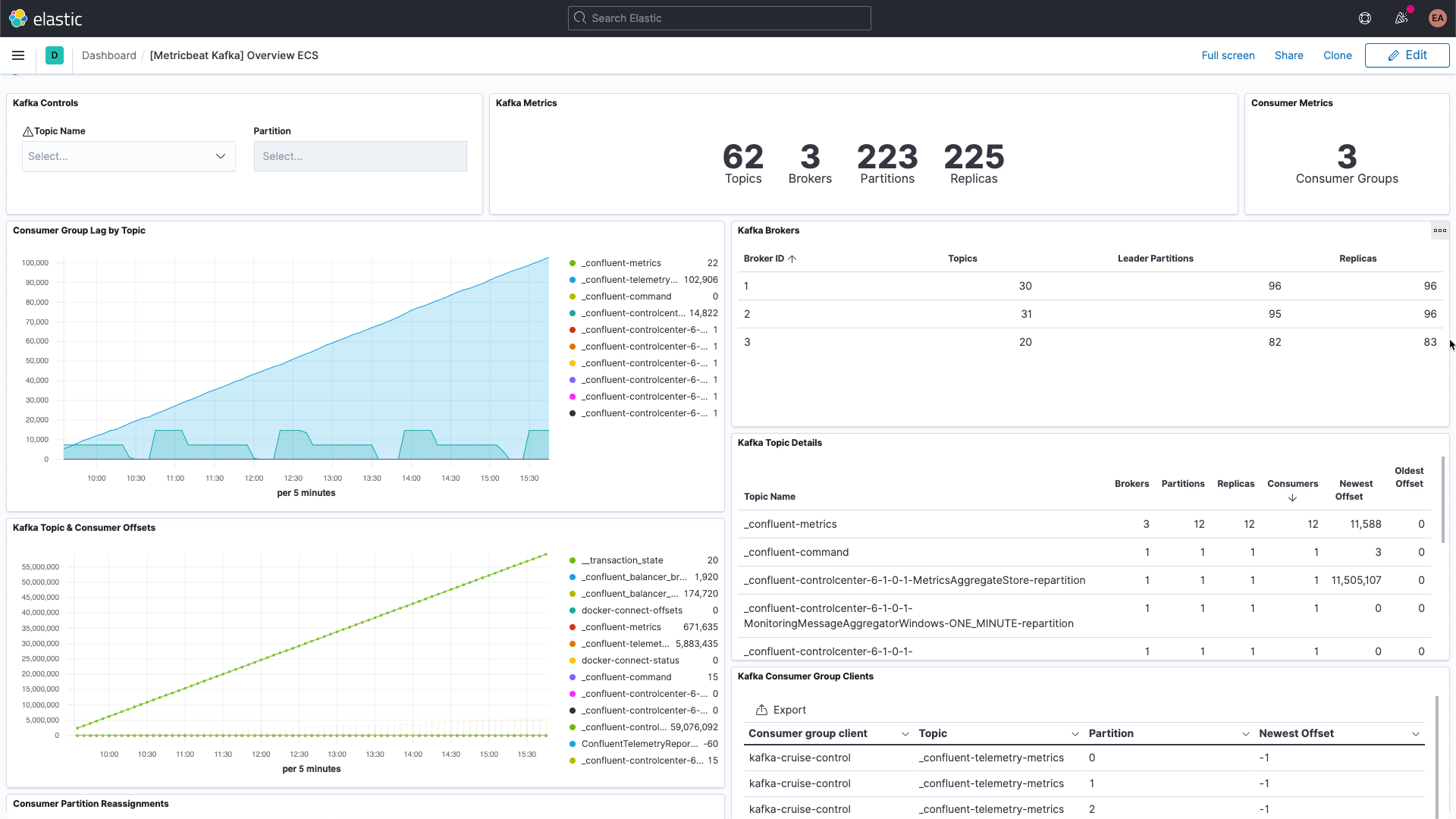
How to monitor containerized Kafka with Elastic Observability 24 March 2021 Learn how to monitor your containerized Kafka cluster with Elastic Observability, including logs and metrics… |
|
Ingesting metrics securely using role-based access control (RBAC) 09 June 2020 You’ve identified the systems metrics you need to monitor, and you’ve consolidated them into the Elastic Stack. In this final post in the series, we’re going to make sure they stay secure in Elasticse… |

|

|
Identifying and monitoring key metrics for your hosts and systems 27 May 2020 Infrastructure monitoring (metrics) is a key part of observability, but do you know which metrics you should be monitoring? In part 1 of this series on metrics with the Elastic Stack, learn what stats… |
|
KubeCon 2019: Elastic Doubles Down on Observability and Orchestration for Kubernetes 19 November 2019 As users adopt Kubernetes initiatives, Elastic products move fast to support their evolving needs. Whether you are trying to migrate Elasticsearch workloads to Kubernetes or want to gain better visibi… |

|
|
Elastic APM 7.2.0 released 25 June 2019 Elastic APM 7.2.0 released, including the beta .NET agent, expanded agent metrics, WebLogic and JBoss support, and support for multiple environments… |
|
Elastic Logs 7.2.0 released 25 June 2019 Elastic Logs 7.2.0 released with improved support for structured logs, customizable column views, new NATS and CoreDNS modules, and CRI-O container log input… |

|

|
Elastic Infrastructure 7.2.0 released 25 June 2019 Elastic Infrastructure 7.2.0 released with Metrics Explorer to quickly build and break down time-series visualizations, plus module for CNCF CoreDNS metrics… |
|
Elastic Infrastructure 7.0 released 10 April 2019 Version 7.0 of the Elastic Stack brings you increased observability into your entire application stack, with new modules (NATS, Microsoft SQL Server, CouchDB, and AWS EC2), an improved Prometheus modu… |

|
|
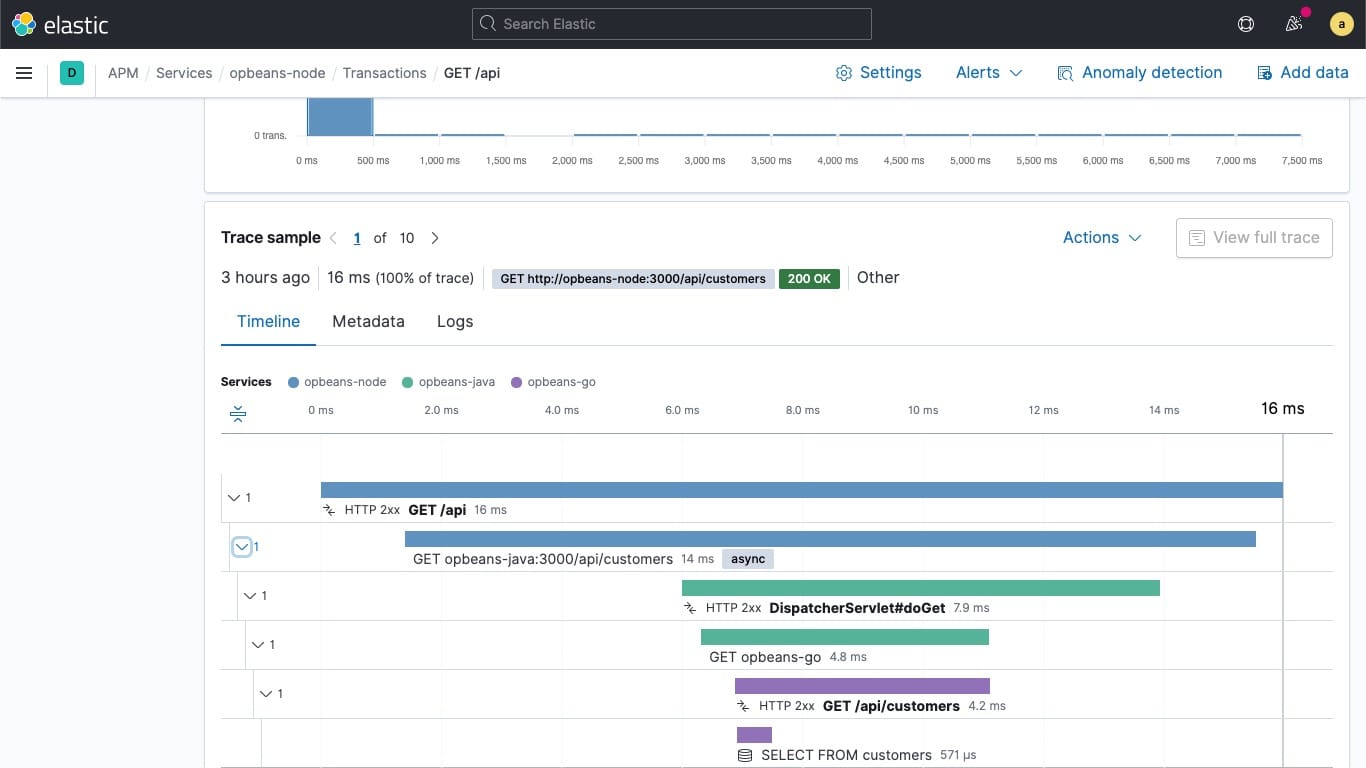
Monitoring Applications with Elasticsearch and Elastic APM 30 January 2019 Application Performance Monitoring (APM) lets see what’s going on inside your application, and helps increase the observability of your entire application stack. Elastic APM increases the observabili… |
|
Tutorial: Getting Started on Elastic Cloud with a Sample Dataset for hosted Elasticsearch and the Elastic Stack 25 May 2018 This step-by-step set of instructions will walk you through setting up an Elastic Cloud account, creating and securing a Elasticsearch cluster, importing data, and visualizing it in Kibana…. |

|
|
|
Here to Help... (An Elastic{ON} Canvas Story) 28 March 2018 … |
|
But First, Coffee... (An Elastic{ON} Canvas Story) 14 March 2018 See how we used Elasticsearch, Kibana, Canvas, and IoT to track beverage metrics at Elastic{ON)… |
|
|
Monitor Your System with Metricbeat and Elastic Cloud 07 September 2017 Learn how to create hosted Elasticsearch deployment s, add users, create Kibana dashboards, and ship system metrics with Metricbeat…. |
|
The ELK Stack on Apcera 2016 This was possibly the first time the ELK Stack was containerized. The original blog was long gone but I still had the collateral so I put it into my repo for posterity. |
|



